
Penetration Testing
Penetration testing, also known as pen testing, security pen testing, and security testing, is a form of ethical hacking. It describes the intentional launching of simulated cyberattacks by “white hat” penetration testers using strategies and tools designed to access or exploit computer systems, networks, websites, and applications. Although the main objective of pen testing is to identify exploitable issues so that effective security controls can be implemented, security professionals can also use penetration testing techniques, along with specialized testing tools, to test the robustness of an organization’s security policies, its regulatory compliance, its employees’ security awareness, and the organization’s ability to identify and respond to security issues and incidents such as unauthorized access, as they occur.
DevSecOps
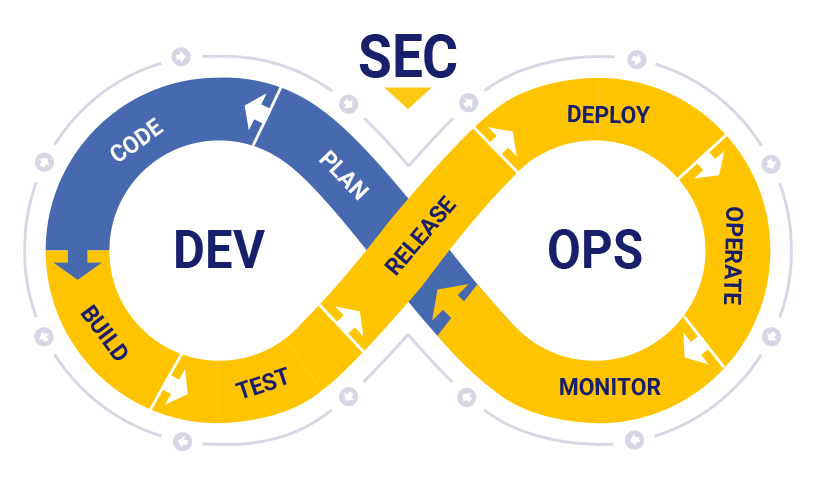
DevSecOps stands for development, security, and operations. It’s an approach to culture, automation, and platform design that integrates security as a shared responsibility throughout the entire IT lifecycle.
Benefits of DevSecOps
Important FAQs on Penetration & Devsecops
What is the goal of DevSecOps?
DevSecOps is designed to make security a part of an organization’s software development workflow. With this approach, software developers and security teams work together to implement security controls into software. Then, an organization can quickly and consistently deliver secure code releases.
Is there a difference between DevOps and DevSecOps?
Yes. DevOps is designed to promote CD, and as such, has become increasingly important to organizations that want to streamline software development. Meanwhile, DevSecOps adds security to the DevOps formula. DevSecOps bridges the gap between security teams and software developers and integrates security into all aspects of software development. By doing so, DevSecOps ensures an organization can build, test and deploy software that is secure, effective and proven to perform.
What types of systems have you performed penetration testing on?
Testing the network layer (firewalls, web servers, email servers, FTP servers, etc.); the application layer (all major development languages, all major web servers, all major operating systems, all major browsers); wireless systems; internal workstations, printers, fax machines; WAR dialing phone numbers, virtual environments including cloud, internet enabled devices, and more. We have tested law enforcement systems, state and municipal government systems, and private sector systems ranging from online gaming to financial institutions.
